Management Gateway firewall – Understanding Networking and Security Configurations
The Management Gateway firewall protects access to management components such vCenter and NSX.
There are two types of management groups: predefined management groups and user-defined management groups. When choosing a source or destination for a management firewall rule, there are three choices: Any, System-Defined, and User-Defined.
System-defined groups simplify the creation of common Management Gateway firewall rules. User-defined groups allow the creation of custom groups based only on an IP address. Such groups are commonly used to provide remote administrators access to management components.
You manage the groups’ configuration on the Inventory tab in the Management Groups section, as seen in the following screenshot:
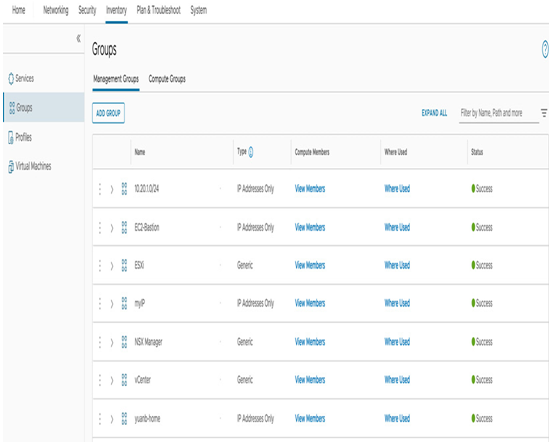
Figure 6.51 – System-Defined Groups Management Gateway
You cannot use any notation or 0.0.0.0/0 as a source for MGW firewall rules – you need to explicitly specify all the sources requiring access to management components by using IP addresses.
Compute Gateway firewall rules
The Compute Gateway firewall protects access to workloads placed behind the CGW. Compute Gateway firewall rules use grouping objects based on various matching criteria, such as IP address, VM instance, VM name, and security tag.
Default security groups are automatically created and include definitions such as the connected VPC prefixes, or S3 prefixes, and they can be used in a CGW firewall rule source or destination, as seen in the following screenshot:
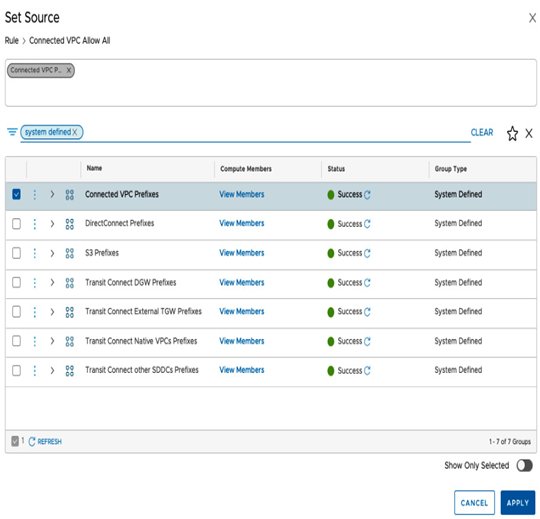
Figure 6.52 – Connected VPC System Defined security group
Customers can manage customized compute groups, under Groups in the Inventory tab, as seen in the following screenshot:
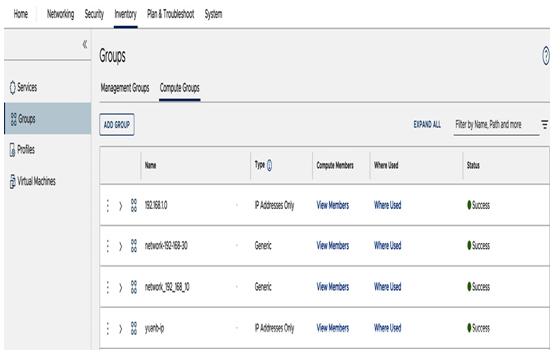
Figure 6.53 – Compute groups
CGW firewall rules are configured in the Gateway Firewall section on the Security tab, as seen in the following screenshot:
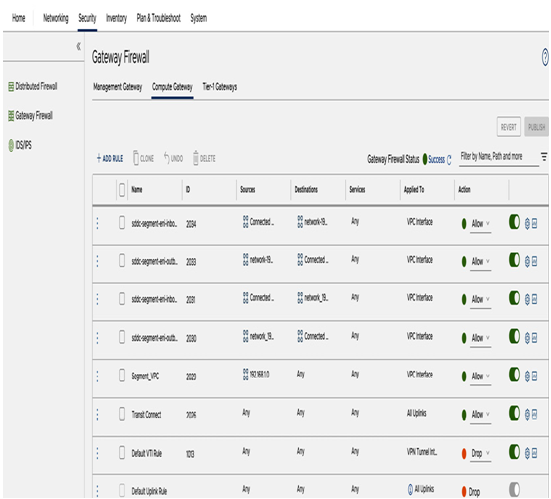
Figure 6.54 – Gateway Firewall settings
Information
Further details on how to create firewall rules can be found at https://docs.vmware.com/en/VMware-Cloud-on-AWS/services/com.vmware.vmc-aws-networking-security/GUID-2D31A9A6-4A80-4B5B-A382-2C5B591F6AEB.html.
Compute firewall rules may be applied selectively to specific interfaces, such as internet, intranet, VPN tunnel, or VPC.
Information
The difference between interfaces can be found at https://docs.vmware.com/en/VMware-Cloud-on-AWS/services/com.vmware.vmc-aws-networking-security/GUID-A5114A98-C885-4244-809B-151068D6A7D7.html.
Tier-1 Gateways are managed on the Tier-1 Gateways tab in the Gateway Firewall section of the Security tab, as seen in the following screenshot:
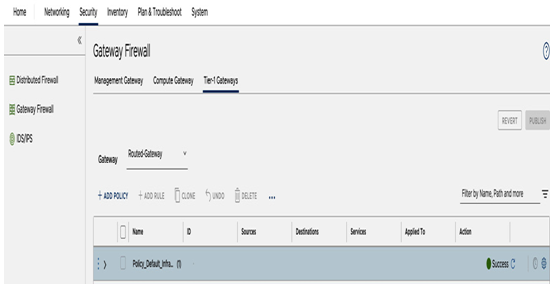
Figure 6.55 – Tier-1 Gateway firewall configuration
After reviewing the NSX firewall configurations, let’s review how to discover and troubleshoot networking and security configurations in the SDDC.