Port mirroring – Understanding Networking and Security Configurations
Port mirroring allows us to copy and redirect packets to a destination monitoring device. This is useful for monitoring and analyzing specific traffic in use cases such as the following:
- Copy it to an advanced firewall (IPS/IDS) to inspect traffic
- For troubleshooting purposes, a copy of a traffic flow can be used
- Mirror traffic to a Wireshark packet capture program to analyze application or packet loss issues
Port mirroring configuration includes specifying the traffic to be monitored (referred to as the source) and determining the direction in which the traffic should be monitored–whether it’s the source, destination, or both.
Additionally, the configuration includes identifying the location to which the monitored traffic should be sent, which is typically a monitoring system. This system can be either remote or local.
There are different types of port mirroring sessions, which include Local Switch Port Analyzer (SPAN), Remote SPAN (RSPAN), and Encapsulated Remote SPAN (ERSPAN). VMware Cloud on AWS leverages ERSPAN to copy traffic leaving or entering a virtual port.
The copied traffic should ideally be sent to a destination VM – usually, a host, workload, or machine running packet capture software such as Wireshark for security analysis or an IDS/IPS device. VMware Cloud on AWS lets customers select one or more VMs to be a source. Each VM will be added to a session of port mirroring.
Information
To allow traffic to be routed from the ESXi hosts to the destination device, a security rule must be placed on the MGW firewall.
The port mirroring configuration is done in the Port Mirroring section on the Plan & Troubleshoot tab, as seen in the following screenshot:
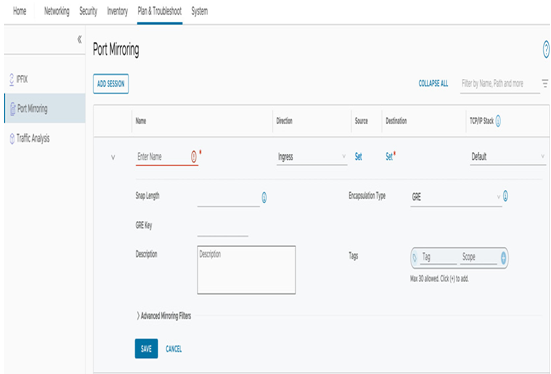
Figure 6.61 – Port mirroring configuration
We have spent some time learning about NSX day two operations, and now we will switch to the NSX distributed firewall feature.
NSX Micro-Segmentation
The Distributed Firewall (DFW) feature is an integral part of NSX in VMware Cloud. It allows East/West firewalling, also known as micro-segmentation. Micro-segmentation enables customers to segment the network and apply security policies at the vNIC level, allowing the creation of security logic beyond the boundaries of Layer 3 segments.
The NSX DFW provides a contextual view of the virtual data center. Workloads can be secured using meaningful metadata instead of just destination and source IP addresses. For example, a VM instance, name, or security tag can be used for security rules, which allows security policies to be built based on business logic. It helps to reduce the impact of security breaches and meet compliance targets. The NSX DFW has powerful capabilities that allow advanced security use cases such as isolation, multi-tenancy, and DMZ Anywhere.
The DFW configuration is located in the Distributed Firewall section on the Security tab, as seen in the following screenshot:
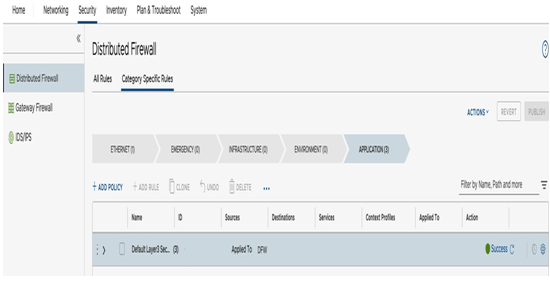
Figure 6.62 – Distributed Firewall configuration
The NSX DFW includes four sections for DFW rules: emergency rules, infrastructure rules, environment rules, and application rules. Each section may have multiple policies and rules.
These sections are used to organize policies. Customers may define all rules within one of these sections and are not required to use this structure.
Information
The default DFW rule permits all traffic.
Rules are processed from the top down. Traffic will see the emergency rules first and application rules last. If no rules have been met, the default rule applies.
Customers can create policies and rules within DFW sections.
Each DFW rule contains a name, source, destination, service (for example, HTTPS), and an action (for example, permit, drop, or refuse). Additionally, Logging can optionally be enabled on each DFW rule. Once enabled, by default, logging is applied in an In-Out (applied to both incoming and outgoing traffic) direction. This can be changed to either In (apply the rule only to incoming traffic) or Out (apply it only to outgoing traffic).
Log entries are sent to the VMware Aria Operations for Logs service (formerly VRealize Log Insight Cloud).
You have now learned the basics of NSX distributed firewall and gained enough knowledge to configure and use NSX capabilities of VMware Cloud on AWS.
Summary
In this chapter, you gained relevant knowledge to be able to design, configure, and operate VMware Cloud on AWS networking based on VMware NSX capabilities. With the recent change in the Networking & Security tab in the SDDC console to the new VMware NSX web interface, it’s vital for administrators to examine the relevant UI elements and update runbooks and documentation. Cloud and networking architects may practically design recommendations, especially around hybrid cloud connectivity.
You are now prepared to use the full potential of VMware Cloud on AWS networking in your organization.
In the next chapter, we will learn about the new integrated services available with VMware Cloud on AWS.

